Risk Management
Risk Management
Approach to Materiality in Customer Privacy
Information that we receive from our customers and business partners is information that should be socially protected and it is also an informational asset for the company. We recognize the proper protection and management of this information as vital.
| Supervising division | Legal/security departments |
|---|---|
| KPI | Number of claims related to informational security |
| FY2018 target | 0 |
| FY2016 result | 0 |
| Boundary (scope) | Advantest Group |
| Relevant policies | Basic Information Security Policy, Privacy Policy |
| Relevant commitments | - |
| Responsible department/division | - |
| Relevant complaint processing policy | We accept contact such as inquiries and complaints at the email address below that is publicized externally. InformationSecurityCommittee@advantest.com |
| Assessment | ✔ |
Risk Management Basic Policy
The Advantest Group will conduct measures to minimize damage should any of the following events occur:
- If damage is caused to buildings or facilities, or if networks and systems stop functioning, thereby making it difficult to continue our business operations, or if there is the possibility of this type of situation occurring due to a disaster or accident;
- If there is the danger of one of our executives or employees being killed or injured or their life or physical health is put at risk due to a disaster or accident;
- If there is an occurrence of scandal or incident that has the potential to become a matter of social concern; or,
- If any event other than those described above were to occur that could cause a significant impact on the business of the Group or its affiliates due to a disaster or accident.
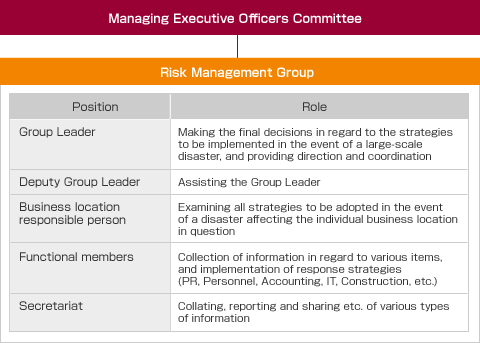
Risk Management System
In December 2001, Advantest established a Risk Management Group with the Company’s president as its head. The Risk Management Group will convene when any of the above events occur, and will consolidate information flows, evaluate the problem, direct the initial response, and formulate recovery plans. The Group will remain in operation until recovery is complete.
Business Continuity Plan
Advantest Corporation established the following basic policy during fiscal 2007 in preparation for large-scale natural disasters. We have devised our business continuity plan based on this policy.
Business Continuity Plan (BCP) — basic policies
- We will place top priority on ensuring human safety should a major disaster strike.
- We will fulfill our responsibility to our stakeholders by ensuring that any impairment to our operations has a minimal adverse impact on our suppliers and other stakeholders.
- We will cooperate with local bodies in regular disaster prevention measures, and if a disaster should strike near any of our locations, we will contribute to local recovery.
After the Great East Japan Earthquake in March 2011, we began reviewing our disaster prevention arrangements. In fiscal 2012, we revised our Business Continuity Plan (BCP) to take into account the possibility of an earthquake directly under Tokyo and flooding along the Tone River, and to ensure the integrity of our supply system even in the event of such disasters. Within the BCP, the following measures are stipulated in line with the basic policy.
| Basic Policy | Specific Measures |
|---|---|
| 1.Ensuring human safety | In addition to continuing with regular disaster prevention drills and safety confirmation drills, we will strengthen crisis management and business continuity systems, making human safety the top priority. |
| 2.Fulfillment of supply responsibilities | When an earthquake occurs, supply systems at our main manufacturing plant (i.e. the Gunma Factory) will continue. In the case of a flood, it is assumed that supply systems will be maintained at alternative manufacturing sites. |
| In preparation for cases where workplace attendance is temporarily impractical because of damage to offices or infrastructure, we will establish an environment allowing high-priority work to be done from home. | |
| 3.Regional & social contributions | Our Gunma R&D Center has been designated by the town of Meiwa as an evacuation shelter in case of flooding, and we contribute to the area by keeping the site ready for flood evacuees. |
Measures Implemented in fiscal 2016
In 2016, management reviews were conducted twice, about the role, policies, and state of activities in August due to restructuring of the Risk Management Group and about the initial response to maintain the head office functions in March. In these activities each quarter, we examined BCP training such as safety that includes the building and equipment related to disaster prevention training in addition to secondary disaster prevention inspections as well as organized and shared information for the initial response of supervisors and each person in charge of business locations. We also conducted training to confirm the safety of our employees in Japan three times in addition to actually confirming the safety of employees in the event of an earthquake to quickly register the safety of each and every employee.
This year, Advantest has also been working to put in place a Business Continuity Management System (BCMS) for the ongoing adjustment of quarterly training and of adjustments to BCM plans etc. based on the results of such training.
Information Security Management Policy
Advantest is fully aware that information we receive from suppliers and information pertaining to our technical and sales operations are important assets; to effectively manage this information we pursue information security practices that include developing regulations, constructing control systems and providing employee training.
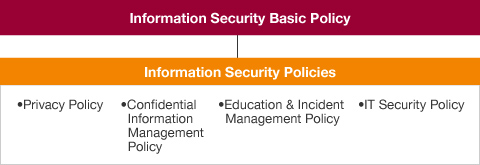
Policies and rules relating to information security
Advantest has established an Information Security Basic Policy. Rules are specified in four policies: our Privacy Policy, Confidential Information Management Policy, Education & Incident Management Policy, and IT Security Policy.
Organization of Information Security Management System
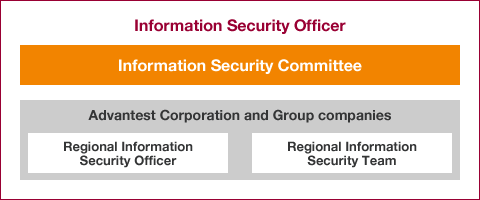
Advantest regards implementation of information security controls as a key management issue, and has accordingly assigned the Senior Executive Officer to act as Information Security Officer responsible for such systems on a global basis.
Moreover, we have set up a system that enables our offices in respective countries to autonomously address information security issues. Under this system, Regional Information Security Officers posted in respective countries bring a variety of viewpoints to the table in the course of deliberating on potential information security measures to be applied on a group-wide basis, and also when considering which policies and rules should be adopted, or otherwise revised or abolished.
Specifically, the head of each Group company’s administration division has been assigned to the position of Regional Information Security Officer, responsible for security management in their respective regions. Meanwhile, members from related divisions in respective countries have been tasked with implementing information security measures.
Organization of Advantest Group Information Security management
Information Security Training
Based on the view that the final barrier for information security is “people”, we aim to thoroughly publicize information security policies and related regulations. We administer information security training on each policy — Privacy Policy, Confidential Information Management Policy, Education & Incident Management Policy, and IT Security Policy — to all employees in Japan and overseas.
Going forward, we intend to continue developing more practical content and offering more pragmatic training through learning activities that entail repeated exposure to information security rules and content covering key topics in that regard.
Initiatives for Strengthening Information Security
In fiscal 2011, we adopted a system whereby internal audit divisions perform information security audits, which enables us to conduct more objective rules-based checks and provide feedback to divisions that have been audited.
In updating our rules governing access to information equipment, we dropped requirements stipulating that employees must use encrypted PCs only, and now allow them to use thin client computer platforms through which they can perform work in secure environments without the prospect of leaving traces of data behind after use. Also, we made sure that our uniform Group-wide guidelines for business-related use of smartphones enable our employees to draw on such devices effectively in a business context, and in a manner that facilitates better customer service.
At some point we will gauge the effectiveness of our information security measures and will consider objective criteria based on which we can evaluate our information security system and pinpoint its strengths and weaknesses.
Confidential Information Protection
Our Information Security Basic Policy defines confidential information as that which has been disclosed by clients under contract along with that which is important to the company; moreover, the policy stipulates that such information be handled in accordance with relevant regulations.
Accordingly, we are committed to ensuring that confidential information is not divulged outside the company by ensuring that it is protected through use of adequate controls governing its storage, disclosure and handling, In fiscal 2016, there were no incidents involving the unauthorized disclosure of important confidential information, etc.
Personal Information Protection
We consider the confidentiality of all personal information entrusted to us to be very important, and accordingly we take steps to ensure that such information is properly protected and managed. In fiscal 2016, there were no incidents involving the unauthorized disclosure of important personal information, etc.
Our commitment to safeguarding personal information entails posting personal information managers in divisions handling such duties, and furthermore ensuring that those managers properly carry out their duties in regard to overseeing such information.
Furthermore, we perform regular audits of personal information control and use practices in the respective divisions, and make improvements whenever deficiencies are discovered.
In Group companies outside of Japan, Regional Information Security Officers work to protect and manage personal information in accordance with the laws, regulations, and demands of each respective country or region.