網站內容顯示
網站內容顯示

Information security management policy
Advantest is fully aware that information we receive from suppliers and that pertaining to our technical and sales operations are considered important assets, and to effectively manage this information we pursue information security practices that include developing regulations, constructing control systems and providing employee training.
Policies and rules relating to information security
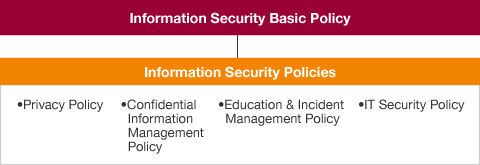
Following our merger with Verigy Ltd. in April 2012, we conducted a review of basic policies, rules and systems relevant to information security. Following the most recent review, we reorganized and integrated existing company regulations, while also establishing four policies — our Privacy Policy, Confidential Information Management Policy, Education & Incident Management Policy, and IT Security Policy — intended to function as sets of rules embodying our Information Security Basic Policy.
Information security management system
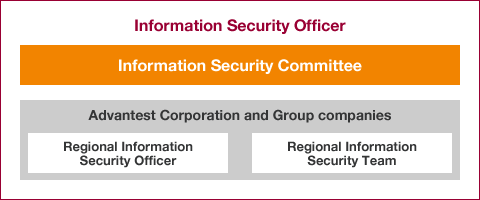
Advantest regards implementation of information security controls as a key management issue, and has accordingly assigned the Senior Executive Officer to act as Information Security Officer responsible for such systems on a global basis.
Moreover, we have set up a system that enables our offices in respective countries to autonomously address information security issues. Under that system, Regional Information Security Officers posted in respective countries bring a variety of viewpoints to the table in the course of deliberating on potential information security measures to be applied on a group-wide basis, and also when considering which policies and rules should be adopted, or otherwise revised or abolished.
Specifically, the head of each Group company's administration division has been assigned to the position of Regional Information Security Officer, responsible for security management in their respective regions. Meanwhile, members from related divisions in respective countries have been tasked with implementing information security measures.
Advantest Group Information security management system
Information security training
Premised on our belief that the people are the key component of information security, we provide training to ensure that employees are familiar with the company's information security policy and associated rules. Accordingly, our global policy on information security, established in response to the 2012 integration of Verigy Ltd., has been made part of training content, which covers:
- safeguarding personal information in accordance with company policy,
- appropriately identify ing confidential information and indicating as such,
- using the right IT tools designed to ensure that information security mishaps are prevented, and
- accurately reporting all information security incidents.
Going forward, we intend continue developing more practical content and offering more pragmatic training through learning activities that entail repeated exposure to information security rules and content covering key topics in that regard.
Initiatives for strengthening information security
In fiscal 2011, we adopted a system whereby internal audit divisions perform information security audits, which enables us to conduct more objective rules-based checks and provide feedback to divisions that have been audited.
In updating our rules governing access to computer equipment, we dropped requirement stipulating that employees must use encrypted PCs only, and now allow them to use thin client computer platforms through which they can perform work in secure environments without the prospect of leaving traces of data behind after use. Also, we made sure that our uniform Group-wide guidelines for business-related use of smartphones enable our employees to draw on such devices effectively in a business context, and in a manner that facilitates better customer service.
At some point we are going to gauge the effectiveness of our information security measures and will consider objective criteria based on which we can evaluate our information security system and pinpoint its strengths and weaknesses.
Confidential information protection
Our Information Security Basic Policy defines confidential information as that which has been disclosed by clients under contract along with that which is important to the company, and moreover the policy stipulates that such information be handled in accordance with relevant regulations.
Accordingly, we are committed to ensuring that confidential information is not divulged outside the company by ensuring that it is protected through use of adequate controls governing its storage, disclosure and handling otherwise.
Personal information protection
We consider the privacy of personal information entrusted to us to be very important, and accordingly take steps to ensure that it is properly protected and managed.
Our commitment to safeguarding personal information entails posting personal information managers in divisions handling such duties, and furthermore ensuring that those managers properly carry out their duties in regard to overseeing such information. Furthermore, we perform regular audits of personal information control and use practices in respective divisions, and make improvements whenever deficiencies are discovered.
In Group companies outside of Japan, Regional Information Security Officers work to protect and manage personal information in accordance with the laws, regulations, and demands of each respective country or region.