웹 내용 전시
웹 내용 전시

Information security management policy
The information we receive from suppliers and Advantest technical and sales information is considered as important assets. Advantest conducts information security measures to effectively manage this information, including the development of regulations, the construction of a management system, and the provision of employee training.
Following the merger with Verigy Ltd. in April 2012, we conducted a review of basic policies and rules relating to information security as well as the management system for the purpose of ensuring the same information security management standards following the merger.
Policies and rules relating to information security
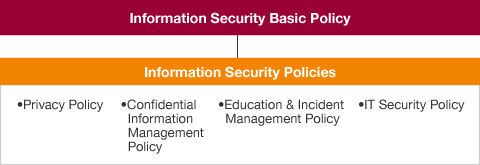
Advantest established the Information Security Basic Policy in July 2003. This policy describes the importance of effective management of information assets and declares that Advantest will work to ensure the confidentiality, completeness, and availability of information assets. Following a recent review, Advantest decided to adopt a set of rules now considered its Information Security Basic Policy. The regulatory documents have been reorganized and integrated to form four policies: the Privacy Policy, Confidential Information Management Policy, Education & Incident Management Policy, and IT Security Policy.
Information security management system
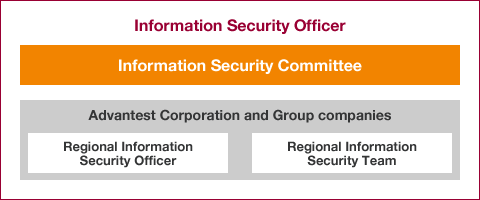
Advantest considers information security management to be an important management issue, and has assigned the Senior Executive Officer that serves as the Head of the Corporate Administration Group as the Information Security Officer. The Information Security Officer is responsible for information security management throughout the Group.
In addition, an Information Security Committee reporting to the Information Security Officer was established during fiscal 2012. This committee is responsible for determining the applicable set of information security measures for the entire Group, and for considering amendments and abolishment of policies and rules. Information Security Committee members were selected from each division, including overseas Group companies, for the purpose of considering information security from various perspectives.
To ensure that information security measures are implemented and policies and rules are fully complied with, we believe that each division needs to work autonomously to achieve information security. Accordingly, a system has been adopted in which information security officers are appointed to the Group’s major business locations.
Specifically, the head of each Group company’s administration division has been assigned as the Regional Information Security Officer. They are responsible for security management in their region and for implementing the measures that are determined by the Information Security Committee. The Regional Information Security Team composed of staff members from related divisions such as the information systems, legal, and human resources divisions are responsible for implementing the information security measures they are entrusted with.
Advantest Group Information security management system
Information security training
The key to information security is people. Based on this belief, Advantest provides training to ensure employees are familiar with the company’s information security policy and associated rules.
In addition to the handling of information devices, during fiscal 2011 training was also given on themes such as information leak risks. Based on case studies of potentially dangerous incidents that occurred at work sites, employees learned about things they should be cautious of and the related laws, regulations, and company rules. In addition, e-learning was introduced to develop a more efficient learning environment.
In the future we plan to develop and conduct training based on more practical content by conducting repetitive learning on rules that should be complied with and covering topics relevant to the current situation.
Initiatives for strengthening information security
In the past, the management of confidential information for each division was confirmed by the security management division visiting the business site and guidance was provided if it was found that improvements were necessary. However, from fiscal 2011 a system was adopted in which Advantest’s audit division would conduct audits on information security. As a result, it has become possible to conduct more objective rules-based checks and provide feedback to the division that was audited.
In the past, rules for the handling of information devices stipulated that it was only possible for employees to use encrypted PCs outside the company to minimize the risk of information leaks due to loss of theft. However, these rules have been revised to allow for the use of thin client PCs. The use of thin client PCs has facilitated work in a secure environment that doesn’t leave any data behind in the devices. In addition, unified Group security standards have been established for the business use of smart phones that have rapidly gained a strong user base. Based on these standards we aim to maintain information security while improving operational efficiency and customer service.
We are studying the adoption of objective evaluation standards in the future that will make it possible to confirm how effective these information security measures have been, the order of priority for measures to be conducted, and the weaknesses and strengths in Advantest’s information security system.
Confidential information protection
Advantest’s Information Security Basic Policy defines information disclosed by clients under contract and the Advantest Group’s material information as confidential information, and stipulates that such information be handled in accordance with relevant regulations.
Specifically, the policy stipulates that the head of the department that holds the confidential information is responsible for security management and declares that confidential information be protected from exposure outside the company or improper access by conducting management, storage, and disclosure that is suitable for each piece of confidential information.
In addition, the importance of confidential information management and the rules that should be complied with are studied repeatedly in the annual information security training.
Personal information protection
Advantest considers the privacy of personal information provided by individuals to be very important, and accordingly takes steps to ensure that it is properly protected and managed.
Management staff responsible for maintaining personal information is assigned to divisions that handle personal information. We ensure that personal information is protected by having these staff members make sure that information is adequately managed. In addition, divisions are audited on a regular basis on the management and use of personal information, and improvements are carried out if any insufficiencies are discovered.
In Group companies overseas, Regional Information Security Officers work to protect and manage personal information in accordance with the laws, regulations, and demands of each respective country or region.